Android - App Fingerprint - Monitor (Pro)
The certificate fingerprint, also known as signature, can be used to detect if the Android app was build and signed by the original developer or someone else. The fingerprint is digitally applied to an app by using a private key (stored in a key store), this ensures the authenticity and integrity of the app. A fingerprint is created by a developer or an organization and is unique to their app.
Validating the fingerprint is easier to set up than checking the app hash, as it can be done locally without having to use an external remote resource for validation.
Monitor
To monitor the certificate fingerprint of the app, AntiCheat has introduced the 'AndroidPackageFingerprintMonitor', which can be found in the 'GUPS.AntiCheat.Monitor.Android' namespace. The monitor reads the signed fingerprint of the app and hashs it using a hash algorithm to make it more human readable, because the fingerprint is stored as binary. Once the fingerprint is read, it notifies observers using the 'AndroidFingerprintStatus'.
Monitor Status
The monitor determines the certificate fingerprint in its Start callback. After determination the observers will be notified with the 'AndroidFingerprintStatus'. The status contains the following properties:
- FailedToRetrieveData: Represents if the certificates fingerprint could not be retrieved or an exception occurred. And no valid value is returned.
- Algorithm: The algorithm used to determine the fingerprint.
- Fingerprint: The determined certificate fingerprint of the app which it was signed with.
Supported Platforms
The monitor is only available on Android platforms.
Requirements
Requires an Android build with at least Android 4.4 (API level 19) (December 2013).
How To Use
The usage is quite simple, attach the 'AndroidPackageFingerprintMonitor' to a child GameObject of the 'AntiCheat-Monitor', assign the used hash algorithm in the 'AntiCheat-Project Settings' and setup the 'AndroidPackageTamperingDetector'.
Requirement
Android with min Android 4.4 (API level 19) (December 2013)
Add Monitor Component
Add the 'AndroidPackageFingerprintMonitor' MonoBehavior from the 'GUPS.AntiCheat.Monitor.Android' namespace to your 'AntiCheat-Monitor' GameObject or better to a child GameObject.
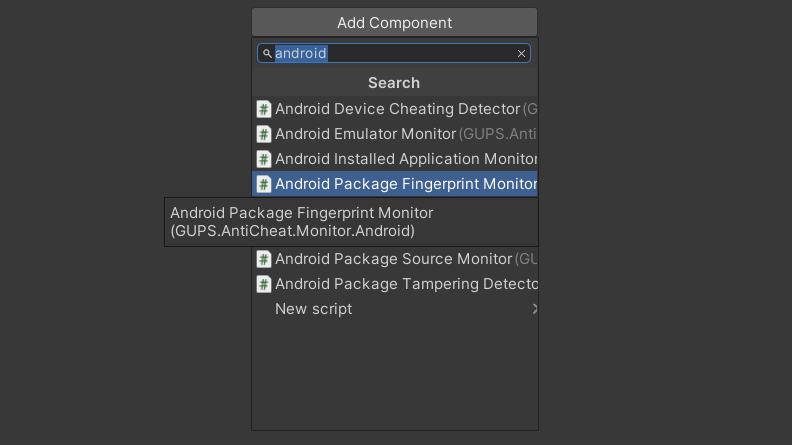
Add the 'AndroidPackageFingerprintMonitor' as Component.
When running on an Android device, the app fingerprint is read in the 'Start' method of the 'AndroidPackageFingerprintMonitor' MonoBehaviour. As soon as the fingerprint was read, an 'AndroidFingerprintStatus' is sent to observers (usually detectors next to the monitor). If the fingerprint could not be read, a status containing the error is also sent.
Hash Algorithm
To calculate the hash of the binary fingerprint, an algorithm is needed. AntiCheat supports the following algorithms:
| Hash-Algorithm | Description |
|---|---|
| None | No hash algorithm is used. |
| MD5 | MD5 hash algorithm. Not recommended for security purposes. |
| SHA1 | SHA1 hash algorithm. Not recommended for security purposes. |
| SHA256 | SHA256 hash algorithm. |
| SHA384 | SHA384 hash algorithm. |
| SHA512 | SHA512 hash algorithm. |
To assign the used algorithm for the fingerprint hash calculation, go to 'Project Settings -> GuardingPearSoftware -> AntiCheat'. Go to the section 'Android - App Fingerprint - Settings'. Activate the 'Verify app fingerprint' checkbox and assign the algorithm you would like to use. Recommended is the SHA256 algorithm.
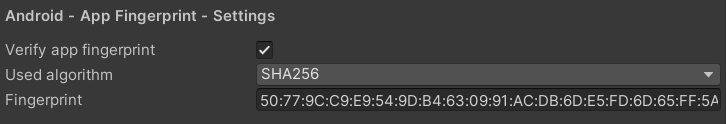
In the AntiCheat Project Settings assign the used algorithm for hashing.
Detect Invalid Fingerprint
To react to the sent status and so validate the calculated fingerprint, you need a detector. To do this, use the 'AndroidPackageTamperingDetector', an aggregated detector that can react to various attempts to tamper with the Android app itself.